Cybersecurity and Zero-Trust Architecture

Cybersecurity and Zero-Trust Architecture
by vivienne 10:18am Jan 08, 2025

As cyber threats grow increasingly sophisticated, traditional approaches to cybersecurity are being challenged. The rise of remote work, cloud services, mobile devices, and complex supply chains has expanded the potential attack surface for cybercriminals, prompting organizations to rethink their security strategies. In response, the Zero-Trust Architecture (ZTA) has emerged as a powerful framework for modern cybersecurity, fundamentally shifting the way organizations protect their data, networks, and digital assets. 
What is Cybersecurity?
Cybersecurity is the practice of protecting systems, networks, and data from digital attacks. These attacks are often aimed at accessing, changing, or destroying sensitive information, extorting money from users, or disrupting normal business operations. Effective cybersecurity strategies employ multiple layers of defense across devices, networks, and software, safeguarding against a variety of threats, including:
· Malware and Ransomware: Malicious software that damages or takes control of a system. Ransomware, in particular, encrypts a victim's files and demands payment for their release.
· Phishing and Social Engineering: Attackers deceive individuals into providing confidential information or access to systems, often by posing as trustworthy entities.
· DDoS (Distributed Denial of Service) Attacks: Attackers overload a network or website with traffic, making it unavailable to legitimate users.
· Insider Threats: Threats from within an organization, such as employees or contractors, who may misuse their access to harm the organization.
· Advanced Persistent Threats (APTs): Sophisticated and long-term cyberattack campaigns, often targeting high-value assets and intellectual property.
To counter these threats, cybersecurity efforts typically involve tools and strategies such as firewalls, encryption, intrusion detection systems, and multi-factor authentication. However, as attackers adapt to traditional defenses, many organizations are moving to more advanced security frameworks, such as the Zero-Trust model. 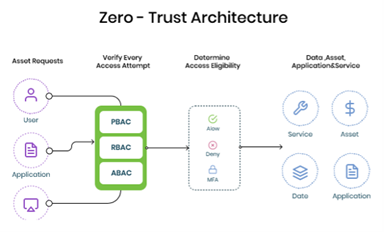
Cybersecurity Best Practices for Individuals and Organizations
Both individuals and organizations play a role in maintaining cybersecurity. Here are some of the most effective best practices:
For Individuals:
· Use strong, unique passwords and change them regularly.
· Enable multi-factor authentication (MFA) for all accounts.
· Be cautious of phishing emails and never click on suspicious links.
· Regularly update software and operating systems to protect against vulnerabilities.
· Use reputable antivirus software and avoid downloading apps or files from untrusted sources.
For Organizations:
· Conduct regular security training to educate employees on safe practices.
· Implement a strong Identity and Access Management (IAM) policy.
· Establish incident response and disaster recovery plans to minimize the impact of breaches.
· Continuously monitor networks and use advanced threat detection tools.
· Regularly back up data to protect against data loss and ransomware attacks. 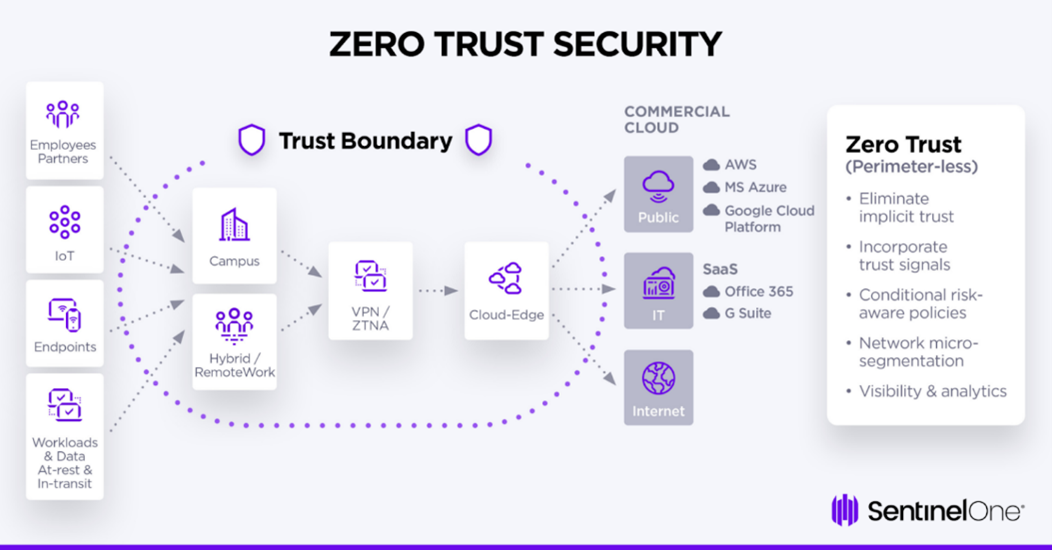
What is Zero-Trust Architecture (ZTA)?
Zero-Trust Architecture is a cybersecurity approach that assumes no user or system—internal or external—should be trusted by default. Unlike traditional models that grant broad access to users within a secure perimeter, ZTA requires strict identity verification for each access request, no matter where the request originates. The foundational principle of Zero-Trust is "never trust, always verify."
In a Zero-Trust Architecture, organizations implement controls that ensure access is granted based on strict verification, minimizing the risk of unauthorized access and lateral movement within the network. The core components of ZTA include:
· Identity and Access Management (IAM): Verifies the identity of users, devices, and systems before granting access. This often involves multi-factor authentication (MFA) and identity verification for every access request, even if the user is already inside the network.
· Least Privilege Access: Grants users the minimum level of access required to perform their jobs, limiting exposure in case of a breach. For instance, a user in the marketing department would not need access to the financial systems, and their permissions are adjusted accordingly.
· Micro-Segmentation: Divides networks into smaller segments, each with its own security controls. This limits the spread of potential attacks, as attackers cannot easily move from one segment to another.
· Continuous Monitoring and Real-Time Analytics: Tracks user behavior and network activity continuously to detect anomalies that may indicate a security threat. For example, if an employee suddenly downloads a large amount of sensitive data, the system can flag or block the action.
· Endpoint Security: Ensures devices accessing the network meet specific security requirements, like using antivirus software, encryption, or updated operating systems. This helps prevent compromised devices from being used as entry points for attacks. 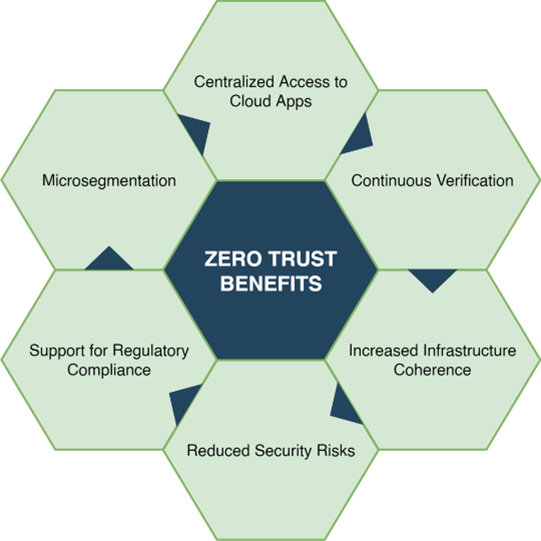
The Shift to Zero-Trust: Why It’s Needed
Traditional cybersecurity models relied heavily on a "castle-and-moat" approach, where an organization's perimeter was the primary line of defense. Inside the perimeter, users had greater freedom, as they were presumed to be trustworthy. However, with cloud services, remote work, and mobile devices, the perimeter has become difficult to define. The shift to Zero-Trust Architecture addresses several critical issues:
· Insider Threats and Lateral Movement: In a Zero-Trust model, access is limited and specific, minimizing the damage a malicious insider or compromised account can do. This prevents attackers from moving easily within a network if they gain access to one part.
· Remote Work and Cloud Environments: With employees working remotely and accessing cloud-based applications, enforcing security at the perimeter is no longer practical. Zero-Trust provides security controls wherever users access data, regardless of location.
· Advanced Threats and Sophisticated Attacks: Cybercriminals are increasingly targeting identity and access management systems to infiltrate networks. Zero-Trust emphasizes identity verification at every step, making it harder for attackers to blend in with legitimate traffic.
Benefits of Zero-Trust Architecture
Zero-Trust offers a range of benefits, making it an increasingly popular choice for modern cybersecurity:
· Reduced Attack Surface: By limiting access to only verified users and devices, Zero-Trust reduces the risk of attackers gaining access to sensitive data.
· Improved Resilience: Micro-segmentation and least privilege access help contain breaches to a single segment, improving overall resilience.
· Compliance and Data Privacy: Zero-Trust architectures often help organizations comply with data privacy regulations by ensuring that access to sensitive data is strictly controlled and logged.
· Flexibility and Scalability: As organizations grow and add new applications, users, or devices, Zero-Trust can adapt without requiring a full overhaul of security policies or infrastructure.
Conclusion
Zero-Trust Architecture represents a paradigm shift in cybersecurity, offering a proactive approach to protecting sensitive data and digital assets in a complex, distributed world. By enforcing strict identity verification, least privilege access, and continuous monitoring, Zero-Trust provides a flexible, scalable framework suited to the demands of modern digital environments. As cyber threats continue to evolve, adopting Zero-Trust Architecture can help organizations stay resilient, reduce their attack surface, and better protect against both external and internal threats.






