Biometric Authentication and Privacy-Enhancing Technologies

Biometric Authentication and Privacy-Enhancing Technologies
by vivienne 11:50am Jan 01, 2025

As digital interactions and transactions proliferate, the demand for secure, seamless authentication has grown. Biometric authentication, which uses unique biological traits (such as fingerprints, facial recognition, or iris scans) for identity verification, has become an increasingly popular solution. However, while biometrics offers enhanced security and convenience, it also raises privacy concerns and potential risks regarding the handling and storage of sensitive data. Privacy-enhancing technologies (PETs) are being developed to address these challenges, helping to protect user data while retaining the benefits of biometric authentication.
This article explores how biometric authentication works, the privacy concerns it raises, and the role of privacy-enhancing technologies in creating a safer and more trustworthy digital ecosystem.
Understanding Biometric Authentication

Biometric authentication is a method of verifying a person’s identity by using their unique biological traits. Instead of relying on something a person knows (like a password) or something they have (like a key card), biometric authentication uses physical or behavioral characteristics that are specific to an individual. Common examples of biometric data used in authentication include:
Fingerprints: Unique ridge patterns on a person’s fingertip.
Facial Recognition: Analyzes the structure, shape, and proportions of a person’s face.
Iris and Retina Scans: Examines unique patterns in the iris or blood vessels in the retina.
Voice Recognition: Identifies a person by analyzing their voice’s pitch, tone, and rhythm.
Behavioral Biometrics: Analyzes unique patterns in behavior, such as typing speed, gait (walking pattern), or mouse movement.
Biometric data is generally stored as templates, which are encoded digital representations of these biological traits. When a user attempts authentication, the system compares a live scan against the stored template to verify identity. Biometrics offers strong authentication because these traits are hard to replicate, and they don’t require users to remember passwords or carry additional devices.
Privacy Concerns in Biometric Authentication
Biometric data is sensitive and often irreplaceable—if compromised, a person can’t “reset” their fingerprint or face as they could with a password. As a result, biometric systems often use encryption and privacy-enhancing technologies to protect biometric data, ensuring secure and responsible handling of this unique information. While biometrics increases security, it presents unique privacy challenges:
· Irreversible Data: Unlike passwords, biometric data cannot be reset or changed. If biometric data is compromised, it can have lifelong implications for the individual’s security.
· Tracking and Surveillance: Biometric systems, especially those based on facial recognition, can potentially enable unauthorized tracking and surveillance. This capability raises concerns about user autonomy and consent, particularly if the data is accessed or used without the user’s knowledge.
· Data Breaches and Misuse: If biometric databases are hacked, sensitive data could be leaked, leading to privacy violations and identity theft. The irreversibility of biometric data makes such breaches particularly concerning.
· Data Retention: Many users are concerned about how long their biometric data is stored, who has access to it, and how it is used beyond initial verification purposes.

Privacy-Enhancing Technologies (PETs)
Privacy-enhancing technologies (PETs) are tools and methods designed to protect individuals' privacy by minimizing the amount of personal data collected, processed, and shared. They allow organizations to maintain data security and compliance while still enabling valuable data insights and interactions. PETs are increasingly used in areas such as biometric authentication, data analysis, and AI to address growing privacy concerns and regulatory requirements. Some of the key PETs relevant to biometric systems include:
1. Federated Learning:
Federated learning is a decentralized approach to machine learning that allows models to be trained across multiple devices or servers without transferring the data to a central location. Instead, each device computes updates to the model based on local data, and only the updates are shared and aggregated to improve the model.
Benefits: Minimizes data exposure by keeping personal data on local devices, reducing the risk of data breaches while still improving models with aggregate insights.
2. Homomorphic Encryption:
Homomorphic encryption is a form of encryption that allows computations to be performed on encrypted data without decrypting it first. The encrypted result can then be decrypted to reveal the correct answer as if the computations were performed on the original data.
Benefits: Protects data during processing, making it possible to perform secure data analysis in environments like cloud computing without exposing sensitive information.
3. Differential Privacy:
Differential privacy adds controlled statistical noise to data sets or queries to prevent the identification of individual users within a data set. This noise is small enough to maintain the utility of the data for analysis but large enough to protect individual privacy.
Benefits: Preserves privacy by ensuring that insights from data analysis do not reveal specific details about any one individual, even in aggregate data reports.
4. Template Protection Techniques:
These techniques modify biometric data templates in ways that make them unreadable to unauthorized users. For instance, cancelable biometrics allow for the creation of temporary templates that can be revoked and replaced if compromised.
Such methods prevent biometric templates from being used across different systems, minimizing the risks associated with data theft or misuse.

The Future of Privacy-Enhanced Biometric Authentication
The integration of PETs into biometric systems is becoming essential for organizations that handle sensitive data, from financial institutions to healthcare providers. Governments are also playing a role by establishing regulations like the GDPR (General Data Protection Regulation) and the CCPA (California Consumer Privacy Act), which set strict guidelines on data privacy and security. The future of privacy-enhanced biometric authentication likely includes:
· Privacy-By-Design: Building privacy protections into biometric systems from the outset, rather than as an afterthought.
· Decentralized Data Storage: Embracing edge computing and distributed data storage to keep user data close to the source and reduce risks of central storage breaches.
· Continuous Authentication: Using multiple biometric factors over time rather than a single factor, enhancing both security and privacy by reducing reliance on a single dataset.
· User Control: Providing users with more control over their biometric data, such as the ability to review, delete, or limit the use of their data.
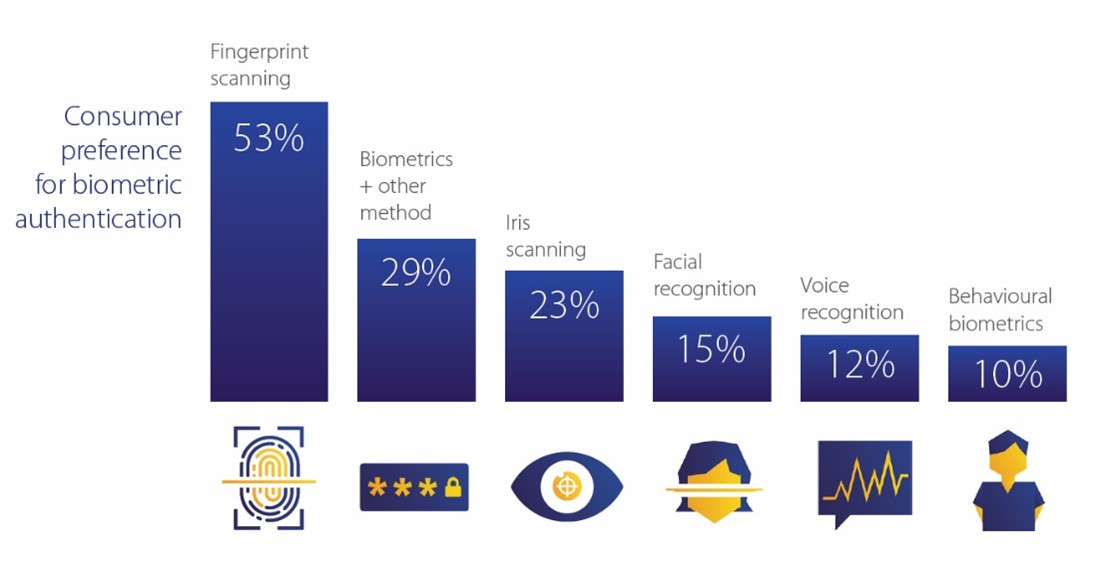
Conclusion
Biometric authentication has transformed digital security by offering a more reliable and user-friendly alternative to traditional passwords. However, its adoption has also highlighted significant privacy concerns, emphasizing the need for robust privacy-enhancing technologies. By integrating PETs into biometric systems, organizations can create a safer, more privacy-focused authentication environment, safeguarding sensitive biometric data while delivering the convenience and security that biometrics promises. As these technologies and frameworks continue to evolve, they will play a crucial role in ensuring that biometric authentication is both effective and privacy-preserving, protecting users’ identities in a digital world that demands both security and respect for individual privacy. Ensuring that biometric systems are privacy-focused is critical for long-term trust and widespread acceptance, making privacy-enhancing technologies an essential aspect of future authentication solutions.